Table of contents
No headings in the article.
Xss is a web security vulnerability that allows attacker to compromise victims in XSS attacker can send java script malicious code, to the victim after sending victim, he will be manipulate, can steal the cookies, account take over, session hijacking
refelected XSS store XSS blind XSS dom XSS
The most common payload is

we need to learn how to create an XSS payload for this I am dropping you a link to a lab where you learn and practice for free and easy to use prompt.ml/0
What is reflected XSS It is a client-side attack where the attacker injects a malicious script into the web application which reflects the payload here an attacker can take whole control of the script that is executed in the victim's browser the cross-site scripting payload can be injected into the URL and search bar like this anywhere where inputs are available
Impacts of reflected XSS:
- Hackers can steal user's necessary credentials
- Hacker can also perform account takeover
- Hackers could also steal cookies and sessions hijacking
- Hackers can extract user's sensitive data
These are some payloads
what is stored XSS this is something where the attacker sends a malicious link victim which reflects in the server here we can understand that in stored XSS, the payload is stored such in the field of the chat box, name, address,
Difference between reflected XSS and stored XSS is simple here in reflected XSS here attacker is attacking the client side, in stored here attacker is attacking to server-side
Stored XSS VS Reflected XSS
Reflected XSS -> STORE== reflect back Stored XSS -> DATABASE -> Reflect Back
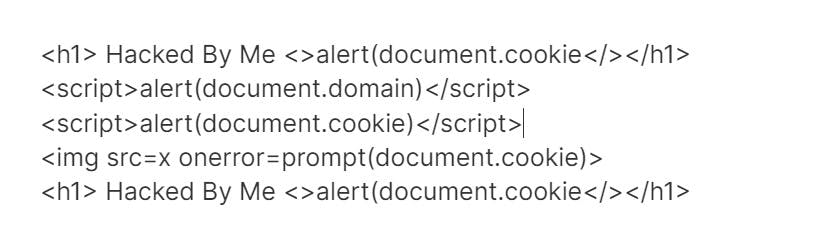
Impacts:
- Hackers can deface the website
- Hackers can steal the user's credentials
- Hackers also can perform hijacking users session's
- Hackers can takedowns user accounts and also take access to victim's computer
Blind XSS: Blind XSS is a vulnerability that is some sort of similar to stored but here the catch is the attacker makes a payload which is connected with his own server he made up payload with his server for example:
attacker target a website -
now he is injecting a malicious script to steal user information
he needs to wait for victims to visit the website and for malicious script to be activated
now victims' information is sent to the attacker for a while to days to fo
Impacts :
- Hackers can perform hijacking user's currents sessions
- Hackers can perform phishing attacks
- Hackers can perform a man in the middle attacks

